Step-by-Step tutorial by expert to understand IP adressing and subnetting Part-I
First of all let us understand IP? IP stands for Internet Protocol. It is a part of TCP/IP stack. IP is a layer 3 protocol according to OSI reference model. IP is mainly responsible for routing. The IP protocol uses specific address called IP address or logical address. Whenever you send any data to another system using any network based application, like internet explorer, FTP client or outlook express etc., the data travels from your network application to the TCP. TCP adds the relevant information to the data and hands it over to the IP.
=========================================================================
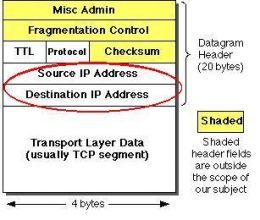
The IP protocol here adds the source and destination IP address. Now let us discuss about IP address in detail.
=========================================================================

As you can see in the illustration, IP address is a 32 bit binary number. But for the ease of human reference it is being represented into dotted decimal notations.Actually it is the dotted decimal notation which is always assigned to the systems by network administrator. Then why do we need to understand the binary form? Definitely this question should arise in your mind. Well as a Cisco Certified Network Associate, you may be required to perform complex tasks related to networking. One of the tasks may be to subnet the IP address. I know now you will be thinking about subnetting. Well here all I can tell you is that subnetting is a process of dividing one network into multiple smaller networks. Let us get back to our core topic. That is, what is IP address? As we discussed earlier, it’s a layer three or logical address used by IP protocol to determine whereabouts of the destination system and the exact system itself. Let us delve into further details.
=========================================================================

As I told you that IP address is a 32 bit binary numbers, which identifies to which logical group the computer belongs to and the exact host. In other words, IP address constitutes of two parts. One part of the address identifies the logical group or network ID of the computer and the other part represents the host itself.Here in the illustration, up to “192.168.0” is network portion and “1” is the host portion of the address. In other words the computer which is assigned with an IP address of 192.168.0.1 belongs to 192.168.0.0 network and its unique identification is “1”. Now the important question is how it is decided that how much portion of the IP address is network address and how much is the host ID? If you look at the binary format of the example IP address, you will find the answer. All continuous “1’s” in the subnet mask decides the network portion of the IP address. The portion of IP address above all continuous ones in subnet mask represents network address. The portion of IP address above all remaining zeroes represents host ID.
=========================================================================

Here you can see that PC-1 and PC-2 are in 192.168.0.0 network. Since both of the computers are sharing the common network id, i.e., 192.168.0, we can call them to be belonging to same logical group. The computers belonging to same logical group can communicate with each other directly without the help of any intermediate device like routers. At the other side PC-3 and PC-4 are in other logical group which is 192.168.1.0. Here PC-3 and PC-4 both share the same network portion, i.e., 192.168.1 and there host ID’s are unique in their network. Remember, in the world of networking, it is not the physical layout which makes different networks, but it is the layer three addresses or logical address which divides computers into different networks. In the illustration if we assign all of the four computers the same network id, i.e., 192.168.0.0 then all of them will become a single network and we will not require a device like router in between. Computers in the same network can communicate with each other without any third device. But computers with different network id must have some type of router in between to act as gateway for the computers of the two networks.
=========================================================================

Suppose here in the diagram if PC-1 wants to send a data packet to PC-2, what will happen? At PC-1 the IP protocol will put its own IP address as source address, PC-2’s IP address as destination IP address in the data packet. While a source and destination layer three addresses are being added to the data packet by say IP protocol, the IP protocol decides whether the packet is destined for the same network or to other network than its own. If the destination network is same then it knows that there is no requirement of any gateway address. It will simply send an ARP broadcast to its own network, asking for the MAC address of the destination machine i.e., PC-2. ARP stands for Address Resolution Protocol and it is a part of the TCP/IP protocol stack. ARP is used to resolve the MAC address from the known IP address. Here in our case the layer three components know what the destination IP address is. But it does not know the MAC address of the computer who’s IP address is 192.168.0.2. So in order to know the destination machines MAC address without which data cannot be moved out of the machine, PC-1 sends ARP broadcast to its own network, asking for the MAC address of the PC-2. The broadcast means request destined for all computers.
=====================================================================================================================
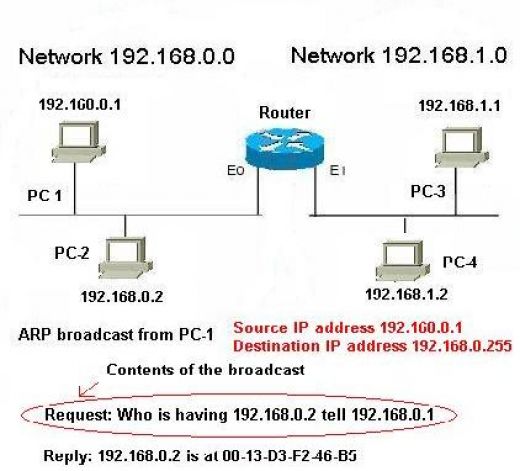
Here in our case the ARP broadcast will be looking something like this. You can see that PC-1 is sending an ARP broadcast to entire network. Entire network here is specified by 255 which is the maximum value for the host portion. Just have a look over the Destination IP address 192.168.0.255. i.e., the packet is destined for the every computer whose Network ID is 192.168.0. This broadcast packet will reach to every computer at the routers E0 side. But the router will not allow this broadcast to be propagated to other side of the router. The ARP broadcast contains a request asking for PC-2’s MAC address. In the last line you can see that PC-2 is responding with its MAC address. This is how computers learn about destination computers MAC address. Then layer two protocols like Ethernet put this address as destination MAC address before data is finally being sent out of the computer. So this whole process was related to the communication between computers in same network. What will happen if PC-1 wanted to communicate with PC-3?
=====================================================================================================================
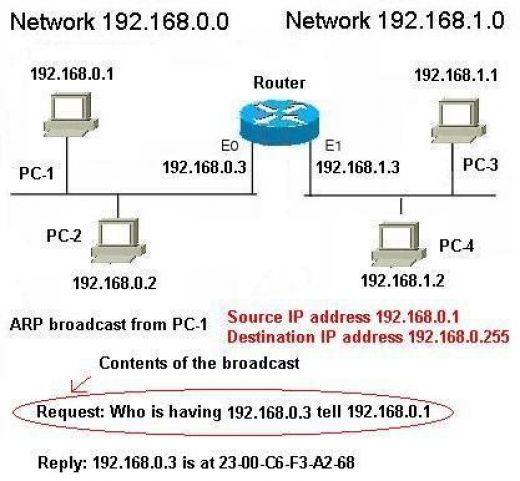
In the case of PC-1 wanted to communicate with PC-3, the Layer three protocols will discover that the destination computer is in other network and it can’t get MAC address of the destination computer directly. Because a computer cannot broadcast any thing other than its own network. And when the router will receive a broadcast destined for 192.168.0.0 network, it will simply drop it. So once PC-1 decided that the destination is in other network, it knows there must be some kind of router in between, and instead of asking for the MAC address of the destination Machine in the ARP broadcast, it should ask for the MAC address of the router. So now in this case PC-1 will send a broadcast to its own network, but instead of asking for the MAC address of the destination computer, it is asking who is having 192.168.0.3? which is the routers address to which side the PC-1’s network is connected. The router is replying with its own MAC address to the PC-1. Once PC-1 obtains the PC-3’s MAC address, it will send the packet on the network. Now this packet will be received by the router, Since the packet’s destination MAC address will match with the router’s MAC address. Now router will check the received packets destination layer three network ID and it will find that the destination network is directly connected to it on Port E1. So router will send an ARP broadcast on E1 destined for the network 192.168.1.255 asking for the MAC address of 192.168.1.1. PC-3 will send its MAC address to the router and router will add that MAC address to the packets destination layer two address field and forward it to the E1 interface. So you would have understood how layer three protocols like IP are used to divide computers into different logical groups. You also understood that routers do not forward broadcasts to other side. Actually we will discuss routing in later chapters. Let us get back to the current topic that is IP addressing.
=====================================================================================================================
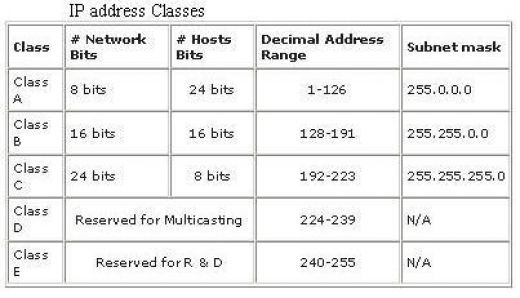
First of all let us get familiar with little of background. The TCP/IP protocols were initially developed as part of the research network developed by the United States Defense Advanced Research Projects Agency (DARPA or ARPA) in the 1970s by pioneering network engineers Vinton Cerf and Bob Kahn. The Designers of the IP protocols created 5 classes of the IP addresses. Namely class A, class B, class C, class D and class E.
======================================================================================================================

Class A is having first 8 bits reserved for network addressing and remaining 24 bits for host addressing. Hence it is having a default subnet mask of 255.0.0.0. Its decimal address range is from 1-126. Network 127.0.0.0 in class A is reserved for loop back address. Loop back address like 127.0.0.1 is used by all operating systems to identify itself. If you successfully ping to this address, it means the TCP/IP protocol is installed properly and it is functional. Class B is having first 16 bits reserved for network addressing and remaining 16 bits for host addressing. Hence it is having a default subnet mask of 255.255.0.0. Its decimal address range is from 128-191.
Class C is having first 24 bits reserved for network addressing and remaining 8 bits for host addressing. Hence it is having a default subnet mask of 255.255.255.0. Class D is reserved for multicasting and is in the range of 224-239. Class E is reserved for R&D purposes and is in the range of 240-255. Out of these five classes, only class A, B, and C are allowed to be used for commercial purposes. We cannot assign class D and E addresses to computers.
=====================================================================================================================
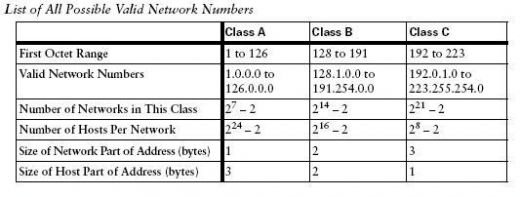
According to the documentations of IP addressing, the first highest order bit in class A must remain “0”, hence we actually get a network range of 2^7-2 equals to 126, i.e., from 1.0.0.0 to 126.0.0.0. and 2^24-2 equals to 16777214 hosts per network. For class B, the first highest order bit must remain “on” and second “off ” that is binary “10” which gives a total of 2^14-2 equals to 16382 networks, i.e., from 128.1.0.0 to 191.254.0.0 and 2^16-2 equals to 65534 hosts per network. For class C, the first and second highest order bit must remain “on” and the third highest order bit “off” that is binary “110” which gives a total of 2^21-2 equals to 2097150 networks, i.e., from 192.0.1.0 to 223.255.254.0 and 2^8 -2 equals to 254 hosts per network. Here you might be thinking why I am subtracting 2 from either number of networks or number of hosts. Well that’s a genuine doubt. Again according to IP documentation all the network bits cannot be either on or off at the same time so we have to subtract two combinations of all zeros and all ones. The same rule applies to host addressing as well so all the host bits cannot be turned on or off at the same time, hence minus two. In the case of hosts, all host bits turned “on” represent a broadcast address and all host bits turned off represent a network address. We cannot assign broadcast address as well as network address to hosts so we have to minus it.
Since all the class A addresses were being assigned to the universities and military organizations in the early days itself, the class A is not available for the public. Almost all class B addresses are also exhausted. Only some of the class C addresses are available. Earlier 2^32 IP addresses were considered quite a large number …!! That’s what was thought by the developers of IP protocol like DoD. When the TCP/IP protocol was developed at DoD, only few computers were there in the universities and other organizations. And not all of them were thinking to connect with each other. So 2^32 really seemed a big number those days. But with the advent of time the popularity of TCP/IP protocol started to soar. Almost every one wanted to be connected and hence every computer required one IP address in order to connect to others, and no more than one computer connected together can use the same IP address. Soon it was realized that in near future the IP address is going to be scarce. So the Scientists came up with a solution to do away with the shortage of IP address.
======================================================================================================================

They kept aside some of the IP addresses from all of the three classes namely class A, B, and C to be used as Private IP addresses. The remaining IP addresses in the above mentioned three classes were reserved to be used on internet and termed as Public IP address. The important thing to remember is that the computers having any IP address within these private ranges cannot connect to internet directly without some sort of network address translation. We will discuss network address translation later. The computers having addresses between these private ranges cannot connect to the internet directly due to the fact that the internet routers are configured to not forward the data packets destined for these private IP addresses. In other words if an internet router receives a packet destined for Private IP address, it will simply drop the packet. And this is implemented to save the IP addresses. You would be wondering how keeping aside some of the IP addresses as private addresses save the overall public IP addresses..? in fact it seems to be decreasing the number of public IP addresses.
======================================================================================================================

Just look at the network and you can yourself figure out how keeping few IP addresses as private saves lot of IP addresses. Here you see a private network comprising of lot of desktop computers is connected to internet through a server which is doing Network Address Translation. The server is having two network adapter cards with two IP addresses. The server’s internal network card is having the IP address within the same Private network as that of Desktop computers. While server’s external network interface card is having a public IP address 202.60.23.1. Using this public IP address, server is connected to internet. All the desktop computers are configured with a gateway as 192.168.0.100. Whenever any desktop computer want to connect to the internet, they simply send the data to NAT server, the server removes the source IP address from the clients packet and replaces it by its own public IP address, then forwards it to the internet. Though all the internal hosts having private IP addresses can connect to internet, but the IP addresses which will be going out as source addresses will be that of NAT server, that is 202.60.23.1. When replies come from the internet for the internal hosts, the NAT server hands over the data packets to the appropriate hosts. This is how thousands of computers in a company having private IP addresses can connect to internet using only single public IP address. Since Packets destined for private IP addresses gets discarded by internet routers, end number of organizations or companies can use the same private IP addresses internally and they will require only single public IP address. So definitely division of IP addresses into Public and Private saves a lot of IP addresses. Private IP addresses also provide a kind of security to the companies, since all the internal hosts having private IP addresses are represented by a single Public IP address. Only that single public IP address remains visible to internet. Though a lot of Public IP addresses are being saved due to private IP addresses but still large numbers of IP addresses are being wasted due to certain reasons. How still the IP addresses are being wasted, I will explain you.
=====================================================================================================================
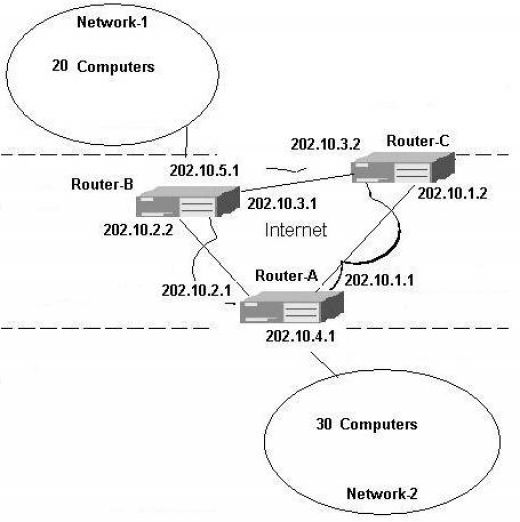
Just have a close look at the network. You can see several internet routers with two end networks attached. The very important thing you will notice in this exhibit is that every internet router’s directly connected interfaces are consuming complete one network. See the connection between Router-B and Router-C, Router-B is having 202.10.3.1 and Router-C is having an IP address of 202.10.3.2 both in the class-C. Out of 254 IP addresses available in the Class-C network, only two IP addresses are being used between Router-B and Router-C. The remaining 252 IP addresses cannot be used anywhere else now, since same network cannot be assigned at multiple sides of the routers. Due to this rule a lot of IP addresses are being wasted between router to router connections. Lot of IP addresses are getting lost at network-1 and network-2 as well. You see that network-1 requires only 20 IP addresses and network-2 requires only 30 IP addresses, the remaining IP addresses at network-1 and network-2 cannot be used any where else, again causing a loss of lot of IP addresses. To save the IP addresses further getting lost this way, a new workaround was done, known as subnetting. Subnetting not only saves the IP addresses, but it also provides better management of the network. In simple words, subnetting is a process of dividing one large network into multiple smaller sub-networks. Just remember that in the network in front of you, lot of IP addresses were getting wasted due to the very less number of IP addresses required on the router interfaces than the number of IP addresses available in each Class-C network. So now we can divide one network into multiple smaller networks and those smaller networks can be assigned at different interfaces of the routers. In the present scenario, we are using almost five (5) class-C networks. This provides almost 254*5 equals to 1270 IP address. And how many addresses are we using? Only 58? So we are using only 58 IP addresses out of total 1270. How many IP addresses are getting wasted? 1270-58 is equal to 1212 IP addresses. So you can see that we are losing almost 1212 IP addresses which cannot be assigned any where else. The solution? Just divide the networks into smaller ones and save lot of IP addresses.



